

Crypto Vulnerability Management Solutions: A Quick Guide

Cryptocurrencies have come a long way, from being considered an unusual investment to becoming a key part of how we pay for things worldwide. This growth shows just how important it is to keep blockchain technology safe. As cryptocurrencies become more common, making sure they're secure is a big deal.
Nowadays, when software and apps are made and updated quickly, it's easier for security problems to pop up. Even though many organizations know how bad cyberattacks can be and understand blockchain and cybersecurity, they sometimes skip checking for weaknesses.
One of the biggest security problems happened with PolyNetwork, where hackers stole over $600 million in cryptocurrencies. This shows just how significant the risk can be.
In this article, we're going to talk about what makes cryptocurrencies vulnerable, especially when it comes to smart contracts, and how to deal with these risks.
What Is Crypto Vulnerability Management?
Crypto vulnerability management is a critical security practice that helps organizations proactively manage and mitigate security risks within their web3 infrastructure. It systematically identifies, assesses, addresses, and reports security vulnerabilities across systems, software, networks, and applications.
The essence of crypto vulnerability management lies in its ability to offer continuous insight into an organization's security posture, enabling the identification and prioritization of vulnerabilities to reduce the potential for exploitation.
Stages of Risk-Based Vulnerability Management
Here’s how risk-based vulnerability management unfolds in the context of crypto:
- Identification: Using automated tools and manual testing to discover vulnerabilities in systems and applications.
- Assessment: Evaluating the identified vulnerabilities to understand their severity and the potential impact on the crypto environment.
- Prioritization: Ranking vulnerabilities based on their risk, considering factors like the ease of exploit, severity of potential impact, and value of the affected crypto assets.
- Remediation: Addressing the highest priority vulnerabilities first, through patching, applying security measures, or sometimes accepting the risk if mitigation isn’t feasible.
- Verification: Ensuring vulnerabilities have been effectively mitigated, and the remediation efforts haven’t introduced new issues.
- Monitoring: Continuously scanning for new vulnerabilities and reassessing the crypto organization's security posture to adjust priorities and strategies as necessary.
Quick Link: Smart Contract Audit Services - What to Expect
Vulnerability Management vs. Vulnerability Assessment
Vulnerability management and vulnerability assessment are critical processes in the crypto world, yet they're often confused with one another. This confusion might stem from their shared goal: identifying weaknesses in systems. However, they serve distinct functions within the broader scope of crypto security.
Vulnerability assessment is the starting point. It's about spotting, listing, and sometimes ranking the vulnerabilities in a system or application. Imagine it as taking a snapshot of the current security weaknesses that exist. This foundational step provides a clear picture of what security issues must be addressed.
Vulnerability management, however, extends much further. It’s an ongoing cycle of finding, assessing, addressing, and monitoring vulnerabilities, but with a critical difference—it includes fixing these vulnerabilities and regularly checking for new ones. This ongoing process is essential for keeping systems secure in the dynamic world of cryptocurrencies, where the threat landscape constantly evolves.
Types Of Crypto Vulnerabilities
Below are some of the prevalent types of crypto vulnerabilities and how attackers can exploit these weaknesses:
Blockchain Network Attacks
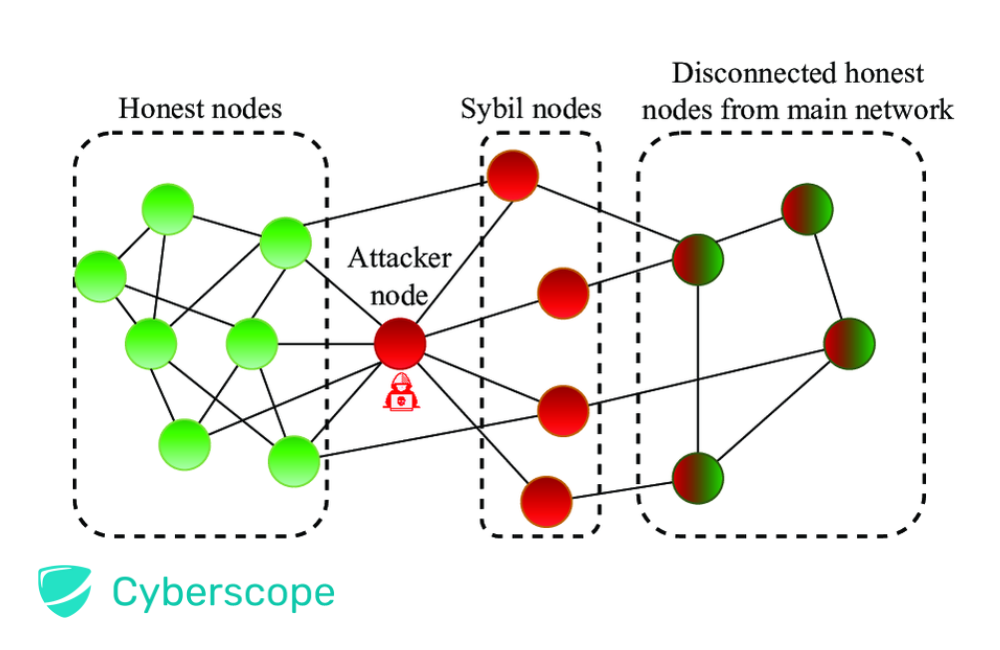
Cybercriminals look for vulnerabilities within blockchain networks and launch attacks, including Distributed Denial of Service (DDoS), transaction malleability, and various consensus attack methods such as Sybil, routing, eclipse, and long-range attacks. They mainly target networks using Proof of Stake (PoS) consensus mechanisms.
Additionally, by manipulating a node's network time counter, attackers can trick it into accepting an incorrect blockchain version, exploiting how cryptocurrencies handle timestamps.
Smart Contract Attacks
Smart contracts, especially those deployed on the Ethereum Blockchain, are vulnerable to attacks due to developer errors in coding. To mitigate these risks, developers must address security vulnerabilities in the development and execution phases with audits.
This requires a rigorous approach to software creation, regular updates, and diligent maintenance to safeguard against unauthorized exploitation of Ethereum-based smart contract code.
User-Wallet Attacks
Attackers frequently target user blockchain wallet login details, employing tactics such as phishing, exploiting vulnerabilities in key generation processes, conducting hot and cold wallet attacks, and dictionary attacks to steal credentials.
Another common tactic is the exploitation of weak user signatures on blockchain networks through various cryptographic methods, which poses significant risks to the security of user assets.
Transaction Verification Attacks
The transaction verification process on the blockchain, which requires consensus among all nodes, presents a vulnerability that hackers can exploit. The most notable example is the 51% attack, where attackers gain control of most of a network's hash rate, enabling them to manipulate transaction verifications.
An attack of this nature on Ethereum Classic (ETC) in August 2020 led to the double spending of over $5.6 million worth of cryptocurrency.
Best Practices to Mitigate Crypto Vulnerabilities
Here are some essential best practices for enhancing security within your blockchain environment:
1. Implement Identity and Access Control Policies
Objective: To manage and regulate access efficiently, ensuring only authorized individuals can access blockchain resources.
Approach: Develop and enforce robust policies that specify how identities are verified and access is granted and revoked, thereby protecting the integrity and confidentiality of sensitive data.
2. Utilize Hardware Security Modules (HSM)
Objective: To secure blockchain identity keys and prevent unauthorized access or tampering.
Approach: Deploy HSMs to manage and store cryptographic keys. These specialized devices are designed to perform cryptographic operations securely, making them indispensable for protecting sensitive information.
3. Enforce API Security
Objective: To safeguard API-based transactions from unauthorized access and breaches.
Approach: Implement stringent identification, authentication, and authorization protocols for all APIs to ensure that only legitimate requests are processed, enhancing transaction security.
4. Implement Privileged Access Management (PAM)
Objective: To control and monitor privileged access within the organization, minimizing the risk of insider threats and breaches.
Approach: Use PAM solutions to grant administrative access only to those who require it for their roles, coupled with continuous monitoring of their activities to detect and respond to suspicious behavior promptly.
5. Adopt Data Classification and Privacy-Preserving Technologies
Objective: To protect confidential and sensitive information from unauthorized access and exposure.
Approach: Classify data based on sensitivity and implement privacy-preserving technologies accordingly. This strategy enables the application of suitable security measures tailored to the data sensitivity level.
6. Secure Smart Contracts
Objective: To prevent unauthorized manipulation of smart contracts and ensure they function as intended.
Approach: Apply access control mechanisms to all aspects of smart contracts, from development to deployment, to safeguard against vulnerabilities and ensure operational integrity.
Common Vulnerability Management Challenges

Here's a closer look at these common challenges and potential strategies to address them:
1. Lack of a Complete Asset Inventory
Challenge: Many organizations struggle with gaining full visibility into their assets across complex IT environments, making it challenging to ensure comprehensive scanning and protection.
Strategy: Implement automated asset discovery tools and maintain an updated inventory. Regularly scanning the environment can help identify unaccounted assets.
2. Resource Prioritization
Challenge: With potentially thousands of vulnerabilities to address, deciding which ones to remediate first can be daunting without established prioritization processes.
Strategy: Adopt risk-based prioritization methods, focusing on vulnerabilities that pose the greatest threat to the most critical assets.
3. Inter-team Coordination
Challenge: Effective vulnerability remediation often requires seamless collaboration between security and IT teams, which can be hindered by poor communication and unclear processes.
Strategy: Establish clear communication channels and responsibilities. Use collaborative platforms and regular meetings to ensure team alignment.
4. Reliance on Manual Processes
Challenge: Manual processes for tracking and remediating vulnerabilities can be time-consuming and prone to errors, leading to delays.
Strategy: Automate vulnerability scanning and the initial remediation phases to increase efficiency and accuracy.
5. Difficulties Getting a Full View of Vulnerabilities
Challenge: Obtaining a unified view of vulnerabilities across the enterprise is particularly challenging in large and complex environments.
Strategy: Implement centralized vulnerability management platforms that aggregate data from various sources, providing a comprehensive overview of the security posture.
6. Dealing with Dynamic Attack Surfaces
Challenge: The continuous emergence of new vulnerabilities complicates monitoring and managing the organization's attack surface.
Strategy: Adopt continuous monitoring solutions and adapt vulnerability management strategies to be proactive rather than reactive.
Quick Link: Top Blockchain Security Companies for Robust Protection
Must-have Features of Vulnerability Management Software
Vulnerability management (VM) tools are indispensable in the cybersecurity arsenal of modern organizations, enabling them to proactively identify, assess, and mitigate vulnerabilities before they can be exploited.
As the digital landscape evolves, so do the essential features for an effective VM solution. Here's a detailed look at the must-have features of vulnerability management software:
Dynamic Discovery and Inventory
VM tools need to be flexible and keep an up-to-date list of all IT assets to keep track of a company's large IT setup. These tools should automatically find and monitor every IT asset, like managed and unmanaged devices, IoT, cloud, on-premises, and mobile devices, right when they start being used. A top-notch VM system should be easy to set up and give a clear overview of all the company's IT assets, spotting and sorting new assets as they join the network.
Asset Visibility
In modern IT setups, tracking assets now cover company-owned devices and a mix of personal devices, third-party gadgets, cloud services, and IoT devices. VM software must provide a broad view across all these IT elements. This lets security teams find, watch, and check all devices and assets on the network. Such a feature is vital to correctly identifying which devices and apps are most at risk of attacks based on their past exposure and known weaknesses.
Attack Vector Coverage
Today's VM systems need to go beyond just checking for software that hasn't been updated. They should cover many different ways attacks can happen. This means looking out for issues like wrong network or hardware settings, weak encryption, the use of simple or repeated passwords, phishing scams, ransomware, denial of service attacks, password reuse, and the risks of spreading threats.
By continuously monitoring and dealing with these various dangers, VM tools can help prevent security problems before they start. They offer ways to protect against attacks from many directions.
Real-Time Monitoring and Analysis
Modern VM software should monitor and analyze all potential attack points in real time, unlike older tools that work in intervals. This method detects possible security risks at any time, ensuring new devices and vulnerabilities are identified and evaluated promptly. Real-time analysis thoroughly assesses security risks across every device, application, and user, covering the entire complex attack landscape.
Advanced Artificial Intelligence and Machine Learning
With the massive volume of data from numerous IT assets, artificial intelligence (AI) and machine learning (ML) are essential. Modern VM tools must apply AI and ML to sift through thousands of data points.
This helps in giving a detailed evaluation and ranking of security risks. Such advanced capabilities put VM systems at the cutting edge of security technology. They enable these systems to recognize new threats, use sophisticated attack techniques, and examine data from both inside and outside sources for threats.
How to Choose the Right Vulnerability Management Software
Choosing the right vulnerability management solution involves evaluating several key factors:
- Quality and Speed: Opt for solutions that offer fast and accurate vulnerability scans with minimal false positives.
- User Experience: Choose a tool that is easy to use for security experts, developers, and operations teams and does not disrupt existing workflows.
- Coverage and Flexibility: Ensure the tool supports various operating systems, infrastructure components, open-source libraries, and programming languages. It should be deployable across on-prem data centers, public clouds, hybrid environments, and as a SaaS solution.
- Compliance: The tool should support compliance standards relevant to your industry (e.g., PCI-DSS) and generate necessary reports. It should also allow for the configuration and automatic enforcement of compliance-aligned policies.
- Prioritization: Look for solutions offering various risk prioritization options, including automated and manual prioritization, based on business criticality, risk severity, exploit availability, and data sensitivity.
- Remediation Guidance: Choose a solution that provides clear, actionable remediation guidance for security staff, operations teams, and developers.
Secure Your Digital Assets with Cyberscope Smart Contract Audits
Cyberscope offers a specialized suite of services designed to bolster the security of blockchain and cryptocurrency operations. Cyberscope plays a pivotal role in the vulnerability management ecosystem, ensuring that the smart contracts—which are integral to the functioning of blockchain systems—are secure and resilient against attacks.
We also offer Penetration testing, which can show you how secure your entire network is. To learn more about it, check out Our Services.
As an individual, you can check Our Solutions, which allows you to check if a project is audited, and other information.

.png%3Falt%3Dmedia&w=640&q=75)

