
Signaturescan
Search for event, error, and function signatures that are stored in the Cyberscope Ethereum Signature Database
IDENTIFY SUSPICIOUS ACTIVITY

Unusual Transaction
A suspicious transaction is taking place in the contract. The sender address is a non-verified contract. The method that has been called from the non-verified contract is the 0xa9059cbb.
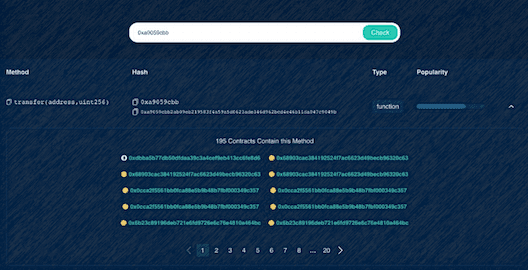
Signature Search
As part of the investigation, the Signaturescan will reveal the actual name of the method. So, the 0xa9059cbb hash belongs to the function transfer(address,uint256).
The investigator will also see all the smart contracts that contain this method.
HOW IT WORKS
Blockchain Code Crawler
Signaturescan runs an automated blockchain code scraper. It connects to the blockchain from a variety of networks and downloads the underlying codebase.
contract ERC20 {
function transfer(address to, uint256 amount)..{
...
}
function approve(address from, uint256 amount)..{
...
}
function increaseAllowance(address from, uint256 v)..{
...
}
}Declarations Extraction
The function, event and error declarations are extracted from the source code.
transfer(address,uint256)approve(address,uint256)increaseAllowance(address,uint256)Hash Generation
The declarations are encoded with Keccak256 hash.
0xa9059cbb0x095ea7b30x39509351Signature Database
The mapping of declaration to hash is stored to the Cyberscope Ethereum Signature Database.
transfer(address,uint256) - 0xa9059cbb[bsc:0x54…63, bsc:0x84…92, …]approve(address,uint256) - 0x095ea7b3[bsc:0x54…63, eth:0x65…93, …]increaseAllowance(address,uint256) - 0x39509351[bsc:0x54…63, matic:0x28…90, …]WHAT IS THE METHOD SIGNATURE
The method calls in the smart contracts are encoded with Keccak256 hash. The first 4 bytes of the hash determine the function that the smart contract will execute.
In unverified smart contracts, the name of the function is not visible, the only information that can be extracted is the signature of the method call.
How we can determine the method name from the signature?
keccak256(method) = hash0xa9059cbb⟶transfer(address,uint256)This is where the Cyberscope Ethereum Signature Database is needed. The user can search for the signature of a "suspicious" method call and find out the actual name of the method that has been called.
hash = keccak256(method)transfer(address,uint256)⟶0xa9059cbb
