

The Most Common DeFi Hacks and How to Protect Against Them

As the internet has increasingly become the primary source for financial exchange, more and more hackers are trying to exploit vulnerabilities in the technology in order to get some quick profit. Recent blockchain analysis shows that more and more cyber attacks are happening on the DeFi space, stealing away millions of investor funds. Today, we take a look at the most common patterns and methods of DeFi attacks that continue to threaten web3 security.
FLASH LOANS
Flash loans have been the preferred method of hackers. A flash loan is basically an uncollateralized loan available for trades by programmers on some DeFi protocols. The hacker will take a loan, exploit a bug by interacting with the DeFi’s smart contracts, pay back the loan and keep the stolen funds are profits. To protect against Flash loans you need to make sure that the dapp that you are investing your money has audited their smart contracts, penetration testing on the end product is also a common counter-measure.
RUGPULLS
Rugpulls have been disrupting the crypto market for the past year in an exponential way. The action of Rugpull is most of the time committed by the project owners, hence protecting against it requires the combination of contract security, checking the locker of the Liquidity pool tokens, and trusting the team, that's why KYC’ed projects tend to perform better and have more security.
STAKING POOLS
Staking is a feature that boosts a project’s roadmap and gives value to its token. History has shown that staking contracts have been the target of hackers as they usually store tokens in the contract, and hackers have been trying to exploit the vulnerabilities of the smart contract. It can be a simple missing check or a permissions modifier that can be exploited into draining the whole balance of all stakers by a hacker. This is why it's so important to Audit your smart contracts.
Cross-Chain Bridges
Cross-chain bridges allow users to transfer cryptocurrency between blockchains. However, they are vulnerable to external attacks. Similarly like the staking contracts, a simple exploit in the code can be detrimental for the security of the project. Millions of dollars can be stolen, just like the Ronin and Wormhole bridge popular hacks.
Phishing attacks
Phishing attacks are on the rise. This fraud is not limited to just DeFi, however, as it can happen in any field of activity. The targets remain the same and that is users. Hackers usually target groups of users on a particular platform. By obtaining users’ personal data or access details, hackers gain access to their finances. This happens not only in DeFi, but in other areas as well. These attacks are very popular, however, protection from them lies solely on users’ shoulders. You can check one of our guides about how to avoid it.
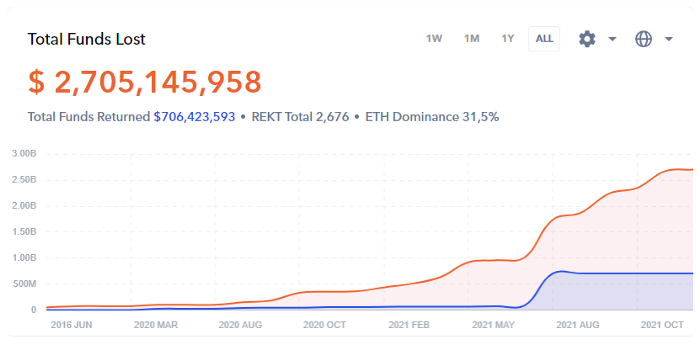
Total funds lost in 2021 from DeFi hacks
How to protect against hacks
Protecting against all of that might seem impossible, but there are some actions you can do. Like you will fasten your seatbelt when you are driving, you need to take all the necessary steps to maximize your chances of not being a victim of a cyber hack. A few actions that you can do is invest in audited DeFi dapps. Ask to read the audit report to better comprehend the vulnerabilities of the smart contract. A common strategy is to also diversify your investments into multiple sources, this way you minimize risk for your capital.
At Cyberscope, it’s our mission to protect retail investors and traders from scammers and fraudsters, so if you ever are in doubt about someone trying to scam you, feel free to send us a message!

.png%3Falt%3Dmedia&w=640&q=75)

