.png%3Falt%3Dmedia&w=640&q=75)

What is a Crypto Contract Scanner and How To Use One

Introduction
The rise of cryptocurrencies has brought about the widespread adoption of smart contracts. These self-executing contracts based on blockchain technology have revolutionized various industries by automating processes and ensuring trustless transactions. However, the security of smart contracts is of paramount importance. In this article, we will explore the concept of crypto contract scanners and learn how to effectively utilize them to enhance smart contract security.
Understanding Crypto Contract Scanners
Crypto contract scanners are specialized tools designed to analyze and assess smart contracts for potential vulnerabilities. These scanners employ various techniques such as static analysis and bytecode analysis to detect security issues within the contract's code. By understanding the inner workings of contract scanners, we can grasp their significance in the broader context of smart contract security.
Smart contract scanners operate by examining the code, identifying potential vulnerabilities, and providing actionable insights to developers. These tools utilize a combination of automated algorithms and predefined patterns to scan for common vulnerabilities, design flaws, and code vulnerabilities. By leveraging these scanning techniques, developers can gain valuable insights into the security of their smart contracts.

Why Use a Crypto Contract Scanner?
The deployment of insecure smart contracts can lead to severe consequences, including financial losses and reputational damage. Crypto contract scanners play a crucial role in mitigating these risks by providing automated vulnerability detection. They help developers identify potential security weaknesses, such as code vulnerabilities and design flaws, before deploying their smart contracts. Utilizing a crypto contract scanner ensures early detection and remediation of vulnerabilities, enhancing the overall security of smart contracts.
Smart contract scanners offer several benefits for developers and organizations:
Early Vulnerability Detection: By scanning smart contracts before deployment, developers can identify potential vulnerabilities and address them proactively. This prevents security breaches and financial losses associated with insecure contracts.
Time and Cost Savings: Automated contract scanners significantly reduce the time and effort required for manual code review. By automating the scanning process, developers can focus on other critical tasks while ensuring contract security.
Compliance with Best Practices: Crypto contract scanners often incorporate industry best practices and security standards. By utilizing these tools, developers can align their smart contracts with recommended coding practices, enhancing their overall security posture.
Enhanced Reputation and Trust: Deploying secure smart contracts demonstrates a commitment to security and builds trust among users and stakeholders. Crypto contract scanners help maintain a reputable image by ensuring the integrity of deployed contracts.
Common Vulnerabilities Detected by Contract Scanners
Crypto contract scanners play a crucial role in identifying vulnerabilities within smart contracts. These scanners employ various techniques to assess the contract's code and configuration, ensuring that potential security risks are detected. Here are some common vulnerabilities that crypto contract scanners check for:
Proxy Contracts: Crypto contract scanners verify if the contract is a proxy, which allows for upgradability but can introduce potential security risks if not implemented correctly. They check if the contract interacts with a proxy contract and assess the associated risks.
Visibility of Contract Code: Scanners examine if the contract's code is visible or public. Keeping the contract code private is crucial for security, as it prevents potential attackers from analyzing the contract's vulnerabilities and exploiting them.
Ownership Renouncement: One important aspect checked by scanners is whether the contract's ownership has been renounced. If the ownership is retained by a specific address, it can pose a security risk as the owner retains control over critical contract functionalities.
Manipulation of Fees: Scanners analyze whether the contract owner has the ability to set fees or transaction costs. The ability to manipulate fees can be a potential vulnerability, as it could result in unfair or arbitrary fee structures that impact contract users.
Minting of Tokens: Crypto contract scanners assess if the contract owner has the power to mint or create new tokens. Unauthorized minting capabilities can lead to inflationary risks or the creation of additional tokens without proper justification.
Burning of Tokens: Scanners examine whether the contract owner can burn or destroy tokens. Unauthorized burning capabilities can result in token supply manipulation and impact the overall value and integrity of the token ecosystem.
Blacklisting of Addresses: Scanners check if the contract owner has the ability to blacklist specific addresses, restricting them from conducting transactions or interacting with the contract. Improper or arbitrary blacklisting can raise concerns of censorship and centralized control.
Mass Blacklisting: Scanners also assess whether the contract owner can perform mass blacklisting, blocking multiple addresses simultaneously. This capability can have significant implications for decentralization and user freedom.
Whitelisting: The ability of the contract owner to whitelist addresses is another vulnerability that scanners analyze. Improper or unfair whitelisting can create disparities in access or privileges within the contract ecosystem.
Transfers Pausing: Scanners check if the contract owner has the power to pause or freeze token transfers. Unauthorized control over transfers can disrupt the normal functioning of the contract and potentially harm users' interests.
Modification of Max Transaction Amount: Scanners examine whether the contract owner can change the maximum transaction amount for token transfers. Unauthorized modification of this parameter can impact the liquidity and trading experience within the token ecosystem.
By assessing these vulnerabilities, crypto contract scanners provide developers with valuable insights into potential risks associated with smart contracts. This information empowers developers to address these vulnerabilities and enhance the security and integrity of their contracts. Crypto contract scanners also play a crucial role in helping investors protect themselves. By identifying vulnerable contracts that allow potential misuse or malicious acts by the owners, these scanners help investors stay safe.

How to Use a Crypto Contract Scanner
Using a crypto contract scanner involves several steps to ensure a comprehensive analysis of the smart contract. Let's explore the key steps involved in using a crypto contract scanner effectively:
Selecting the Right Scanning Tool: Choose a reputable and reliable crypto contract scanning tool that supports the targeted blockchain platform. Consider factors such as scanning capabilities and community reviews when making your selection.
Preparing the Smart Contract: Compile the smart contract and generate the bytecode or machine-readable format required for scanning. Ensure that the contract is properly tested and adheres to best coding practices before proceeding. Most reputable scanners work with deployed addresses as well as source code input.
Initiating the Scan: Run the scanner to analyze the smart contract's code and identify potential vulnerabilities. The scanning process may take some time, depending on the complexity of the contract and the scanning tool's capabilities.
Analyzing the Scan Results: Review the scan results provided by the tool. Pay close attention to identified vulnerabilities. Prioritize addressing critical vulnerabilities that pose significant security risks.
Iterative Scanning and Continuous Improvement: Perform regular scans throughout the development lifecycle and after each code modification. This ensures ongoing security assessment and continuous improvement of the smart contract's security.
If you are an investor, you can use the scanner to check any project’s contract, without any charge. That way, you can have an extra layer of security before you decide to invest in a project.
Choosing a Crypto Contract Scanner
When it comes to selecting a crypto contract scanner, it's important to consider the available options and choose a reliable and effective solution. Here are three popular crypto contract scanners to consider:
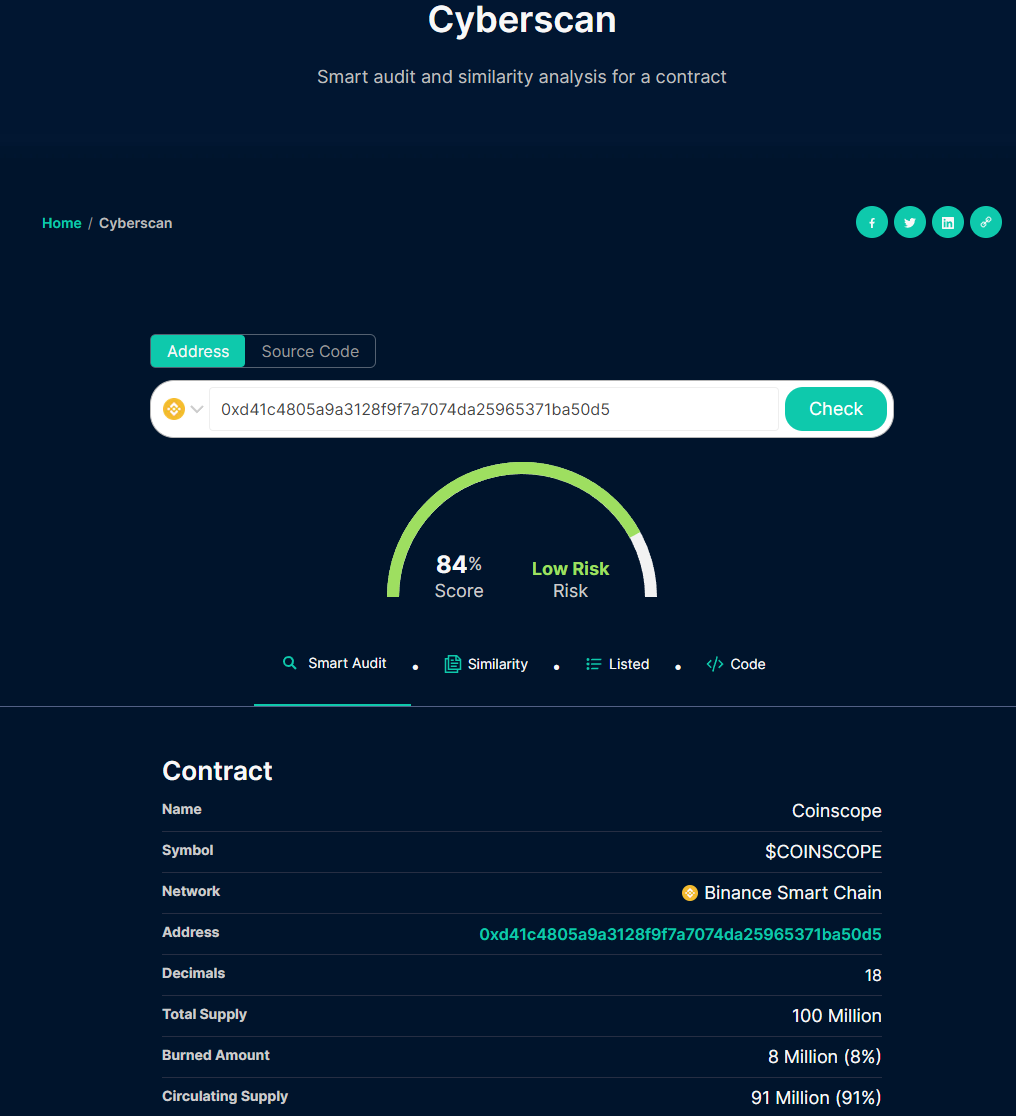
\ Cyberscan: Cyberscan, developed by Cyberscope, is a powerful and comprehensive crypto contract scanner. With its advanced scanning capabilities and user-friendly interface, Cyberscan offers a reliable solution for identifying vulnerabilities and potential risks in smart contracts. It provides detailed reports and recommendations, allowing users to make informed decisions about the security of their contracts.
\ Cyberscan is also featured on CoinMarketCap and GeckoTerminal to provide ratings on the smart contracts of listed projects. That makes Cyberscan the leading tool in the blockchain space, trusted by millions of users worldwide.
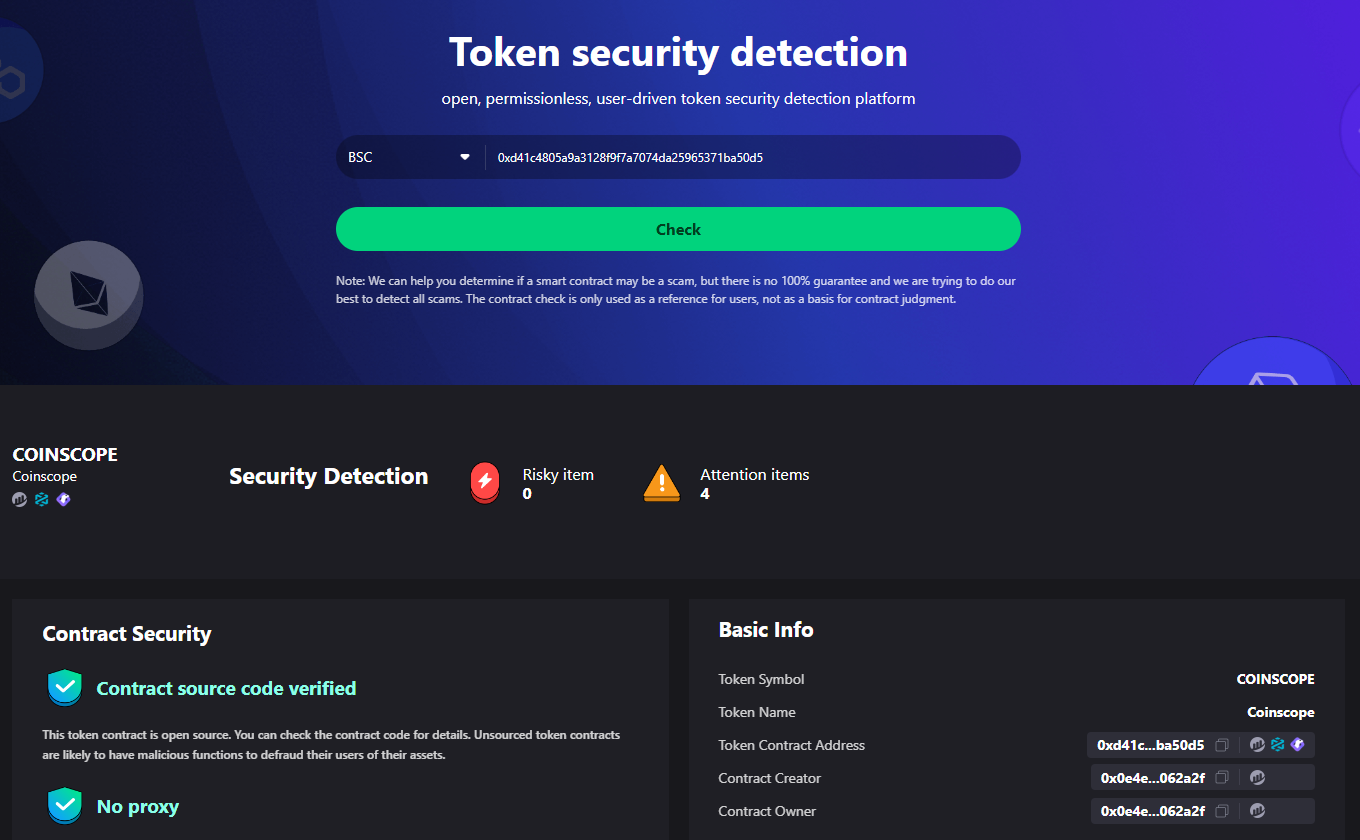
GoPlusLabs: GoPlusLabs offer another widely used crypto contract scanner. It offers a range of analysis features and can detect various vulnerabilities in smart contracts. With its command-line interface, it provides flexibility and allows for in-depth analysis of contract code. It generates detailed reports highlighting potential issues and offers suggestions for remediation.

CoinTool: CoinTool is a popular blockchain platform that includes a powerful crypto contract scanner. It utilizes a combination of static and dynamic analysis techniques to identify vulnerabilities in smart contracts. CoinTools’ automated audit report provides valuable feedback during development, helping developers address potential security risks early on.
Limitations of Crypto Contract Scanners
While crypto contract scanners provide valuable automated security assessments, it's crucial to acknowledge their limitations. These scanners rely on predefined patterns and algorithms, which may result in false positives or false negatives. Additionally, some vulnerabilities require manual review or human auditing to identify them effectively. To ensure comprehensive smart contract security, a combination of automated scanning tools, manual code review, and third-party audits is recommended.
Conclusion
Crypto contract scanners serve as invaluable tools for enhancing the security of smart contracts. By utilizing these scanners, developers can detect potential vulnerabilities, ensure compliance with security best practices, and protect their projects from financial losses and reputational damage. Incorporating crypto contract scanning into the smart contract development lifecycle empowers developers to deliver robust and secure solutions. For investors, using crypto contract scanners not only helps them stay vigilant but also allows them to prioritize smart contract security and make more informed investment decisions.



.jpg%3Falt%3Dmedia&w=640&q=75)