

Security Audit Reports: What to Look For
.png%3Falt%3Dmedia&w=3840&q=75)
Introduction
In the world of decentralized finance (DeFi), security is of paramount importance to ensure the protection of user funds and the trustworthiness of the overall ecosystem. This is especially true in the context of smart contracts, which are often used to execute complex financial transactions in DeFi applications. Given the potential for significant financial losses in the event of a security breach, it is crucial to conduct regular security audits of smart contracts to identify vulnerabilities and suggest improvements to mitigate risks. These audit reports serve as a vital tool for reducing potential risks and building trust in the DeFi ecosystem, as they provide developers and users with valuable insights into the security of the smart contract code. By staying vigilant and up-to-date with emerging threats and vulnerabilities, ongoing security assessments can help maintain the integrity of DeFi applications built on smart contract technology.
Overall, security audit reports are crucial for boosting the security and resilience of the DeFi ecosystem, giving customers assurance about the protection of their money, and encouraging the further use of smart contracts. In this blog post, we’ll explore what to look for in security audit reports and how to review them.

Security Audit Report Components
A security audit report typically consists of several components, including an overview of the audit's purpose, scope, and key findings, as well as a detailed description of the audit's scope.
Overview
The overview section of a security audit report is an essential part of the report that serves as an introduction to the audit and provides context for the rest of the report. The overview section is critical in setting the tone for the report and establishing expectations for the stakeholders. It provides stakeholders with an overview of the audit's purpose, the most important conclusions, and the extent of the review. As a result of that, stakeholders can quickly grasp the report's contents and understand its implications.
Scope
The scope section of a security audit report is a critical component that outlines the audit's objectives and coverage, which sets the tone for the remainder of the report. This section generally includes a detailed list of the system or application components reviewed as part of the audit, providing stakeholders with a clear understanding of the areas evaluated. Additionally, the section describes the testing methodologies employed during the audit, which helps stakeholders assess the thoroughness of the testing and the types of vulnerabilities or flaws examined. The section identifies any limitations or exclusions that may have impacted the audit's findings. By providing a comprehensive overview of the audit's scope and limitations, the scope section enables stakeholders to interpret the report's contents accurately and make informed decisions regarding the system or application's security posture.
Background
Background information is an essential element of the overview section in a security audit report. It provides context and historical information about the system or application being audited, including its environment, previous security evaluations, and any relevant contextual information. This information is crucial in helping stakeholders understand the audit's scope and purpose.
Key findings
They are an integral part of the security audit report as they provide stakeholders with a summary of the audit's primary conclusions. This section draws attention to any significant flaws or vulnerabilities discovered during the audit and gives stakeholders a general idea of the report's contents. Key findings can also include recommendations for addressing the identified security issues, helping stakeholders understand the next steps required to improve the system or application's security posture.

Findings of Audit Reports
A security audit report's findings section lists particular security flaws and issues that were discovered during the assessment. Typically, this section has the following elements:
Summary of Vulnerabilities: In this section, you will find an overview of the vulnerabilities found during the audit, including their seriousness and potential effects on the security of the system.
Detailed Vulnerability Descriptions: Here you will find the specific components of the code that are affected, the vulnerability's underlying cause and all included in the thorough vulnerability descriptions.
Recommendations: Finally, the audit firm provides specific recommendations for addressing the vulnerabilities that have been identified, along with guidance on how to prioritize them and effectively implement the solutions.
The findings section of a security audit report is essential for giving stakeholders practical information to resolve vulnerabilities found and enhance the smart contract’s overall security posture.
Examples of Audit Reports and Findings
The following reports summarize the findings of different audits, including any discrepancies or weaknesses identified in the audited area. Here are some findings from Cyberscope’s audit reports:
Finding 1 - Unsafe Indexing Assumption

Description
The contract assumes that the desired allocations indexes are identical to the market's tokens indexes. This assumption could be broken if the desired allocations or market tokens change without updating the corresponding structures. As a result, the entire contract will yield to an unexpected state.
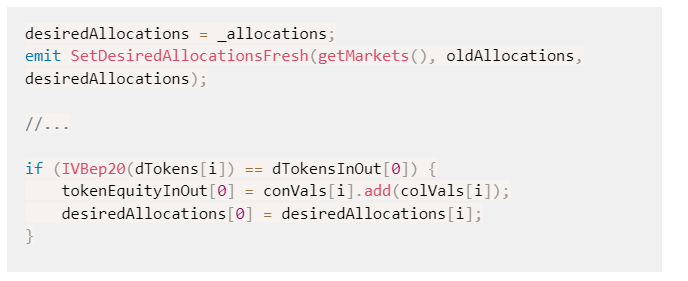
Recommendation
The team is advised to carefully investigate the circumstances where the indexes could be diverse. A recommended way could be to allow only synchronized modifications of these properties.
Finding 2 - Potential Transfer Amount Inconsistency
Description
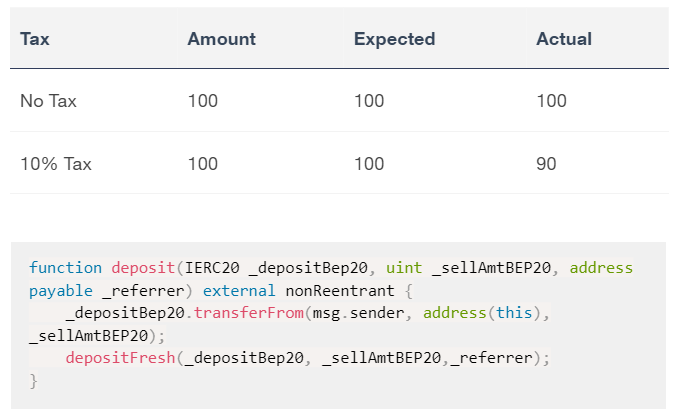
The transfer() and transferFrom() functions are used to transfer a specified amount of tokens to an address. The fee or tax is an amount that is charged to the sender of an ERC20 token when tokens are transferred to another address. According to the specification, the transferred amount could potentially be less than the expected amount. This may produce inconsistency between the expected and the actual behaviour.
The following example depicts the diversion between the expected and actual amount.
Recommendation
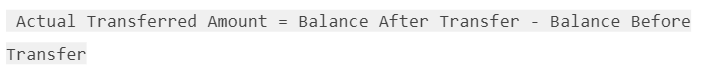
The team is advised to take into consideration the actual amount that has been transferred instead of the expected.
It is important to note that an ERC20 transfer tax is not a standard feature of the ERC20 specification, and it is not universally implemented by all ERC20 contracts. Therefore, the contract could produce the actual amount by calculating the difference between the transfer call.
Finding 3 - Misleading Lock Period
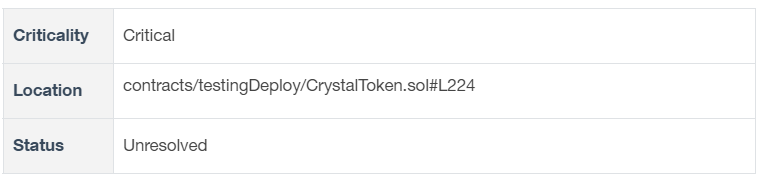
Description
The contract uses the lastUnlockTime[address] variable to determine when the locker will be released for each address. In the method that calculates the duration that has elapsed, the contract subtracts the lastUnlockTime[address] from the current timestamp. The algorithm assumes that it subtracts two timestamps.

The block.number. variable returns the current block number, which is a sequential number assigned to each block in the blockchain. The "block.timestamp" variable, on the other hand, returns the timestamp of the current block, which is a value representing the number of seconds since the Unix epoch (January 1, 1970) at the time the block was mined.
The block.number. can be used to determine the relative time between blocks, but the block.timestamp. can be used to determine the actual time at which a block was mined.
Recommendation
The team is advised to use the same unit across the calculations since the difference between the block number and the current timestamp may produce unexpected behaviour.
Conclusion
To protect users' funds and build trust in the DeFi ecosystem, it is essential to ensure the security of smart contracts. When conducting a security audit of smart contracts, it is important to consider a range of factors, including vulnerability assessments and code reviews.
Finding smart contract flaws and making recommendations for tightening security controls are both important tasks accomplished by security audit reports. DeFi projects benefit from regular, thorough security evaluations that enable them to spot and eliminate any dangers before scammers exploit them. In the end, this increases the ecosystem's confidence and trust in the DeFi platform. If you want to get a security audit report for your contract you can send a message to [email protected].

.png%3Falt%3Dmedia&w=640&q=75)

