

What Is an ERC-20 Token And How Can You Create One?

Do you ever wonder what an ERC-20 token is and how it functions within the vast landscape of blockchain technology? In a world where digital assets are becoming increasingly prevalent, understanding the fundamentals of ERC-20 tokens is paramount. These tokens, built on the Ethereum blockchain, play a pivotal role in shaping the future of decentralized finance, tokenization, and digital asset management.
\ In this exploration, we'll unravel the significance of ERC-20 tokens, delve into their key characteristics, navigate the process of creating these tokens, and examine their profound impact on the burgeoning realm of decentralized finance (DeFi). Join us on a journey through the intricate world of ERC-20 tokens, where innovation meets decentralization, and possibilities abound in the ever-evolving landscape of blockchain technology.
What is an ERC-20 Token?
ERC-20 stands for Ethereum Request for Comments 20, which is a technical standard used for creating and implementing smart contracts on the Ethereum blockchain. This standard defines a set of rules and functions that Ethereum-based tokens must follow to ensure compatibility with various platforms, exchanges, and wallets.
The significance of ERC-20 tokens in the cryptocurrency ecosystem is manifold. Firstly, ERC-20 tokens have standardized the process of token creation, making it easier for developers to issue new tokens on the Ethereum blockchain. This standardization has fueled the rapid growth of tokenization, enabling the representation of a wide range of assets, including cryptocurrencies, digital assets, and even real-world assets, on the blockchain.
Secondly, ERC-20 tokens have played a pivotal role in fostering interoperability within the Ethereum ecosystem. Since all ERC-20 tokens adhere to the same set of rules and functions, they can be seamlessly integrated into decentralized applications (DApps), decentralized exchanges (DEXs), and other Ethereum-based services. This interoperability has contributed to the vibrant ecosystem of Ethereum, driving adoption and innovation across various sectors, including decentralized finance (DeFi), gaming, and non-fungible tokens (NFTs).
Furthermore, ERC-20 tokens have become the standard for fundraising through initial coin offerings (ICOs) and token sales, providing a convenient and efficient way for projects to raise capital and distribute tokens to investors. The widespread acceptance and support for ERC-20 tokens on major cryptocurrency exchanges and wallets have also contributed to their liquidity and accessibility, making them a preferred choice for both investors and developers.

What are the Key Points About ERC-20 Tokens?
- Standardization: ERC-20 is a technical standard proposed by Ethereum developers to ensure compatibility and interoperability between different tokens and smart contracts on the Ethereum blockchain. This standardization simplifies the development process for token creators and enhances the usability of tokens within the Ethereum ecosystem.
- Basic Functions: ERC-20 tokens must implement a specific set of functions to comply with the standard. These functions include totalSupply (to get the total token supply), balanceOf (to check the token balance of a particular address), transfer (to transfer tokens from one address to another), transferFrom (to allow a designated spender to transfer tokens on behalf of the token owner), approve (to approve a designated spender to withdraw tokens from the token owner's account), and allowance (to check the amount of tokens approved for withdrawal by a designated spender).
- Widespread Use: ERC-20 has become one of the most widely adopted token standards in the blockchain space, especially within the Ethereum ecosystem. Many tokens issued through ICOs, token sales, and tokenization projects are ERC-20 compliant. This widespread adoption has contributed to the growth and development of decentralized finance (DeFi), tokenization, and blockchain-based applications.
- Compatibility: ERC-20 tokens are compatible with various Ethereum wallets, exchanges, and smart contracts that support the standard. This compatibility ensures seamless integration and transferability of ERC-20 tokens across different platforms and services within the Ethereum ecosystem.
- Token Creation: To create an ERC-20 token, developers write a smart contract using Solidity (Ethereum's programming language) that adheres to the ERC-20 standard. The smart contract defines parameters such as the token's name, symbol, decimal places, initial supply, and functions for token transfers and management. Once the contract is deployed to the Ethereum blockchain, the ERC-20 token becomes operational and can be interacted with by users and applications.
- Interchangeability: ERC-20 tokens are fungible, meaning that each token is identical and can be exchanged on a one-to-one basis. This interchangeability enables seamless trading and interchange of ERC-20 tokens on decentralized exchanges (DEXs), centralized exchanges, and peer-to-peer transactions.
In summary, ERC-20 tokens provide a standardized framework for creating and interacting with digital assets on the Ethereum blockchain, fostering innovation, interoperability, and usability within the decentralized ecosystem.
What is the ERC-20 Standard?
The ERC-20 standard, also known as Ethereum Request for Comment 20, is a technical specification governing the creation and operation of tokens on the Ethereum blockchain. Proposed by Vitalik Buterin and Fabian Vogelsteller in 2015, ERC-20 establishes a common set of rules and functions that Ethereum-based tokens must adhere to in order to ensure interoperability and compatibility with other tokens, wallets, and decentralized applications (DApps) within the Ethereum ecosystem. These rules define functions such as transferring tokens, checking balances, and authorizing token spending, providing a standardized framework for token issuance and management.
With its widespread adoption, the ERC-20 standard has become the de facto standard for creating tokens on Ethereum, powering a diverse array of digital assets, including cryptocurrencies, utility tokens, and security tokens. Its simplicity, flexibility, and compatibility have contributed to the exponential growth of tokenized assets and decentralized finance (DeFi) applications built on the Ethereum blockchain, solidifying its position as a cornerstone of the decentralized web.
How to Create Your Own ERC-20 Tokens?
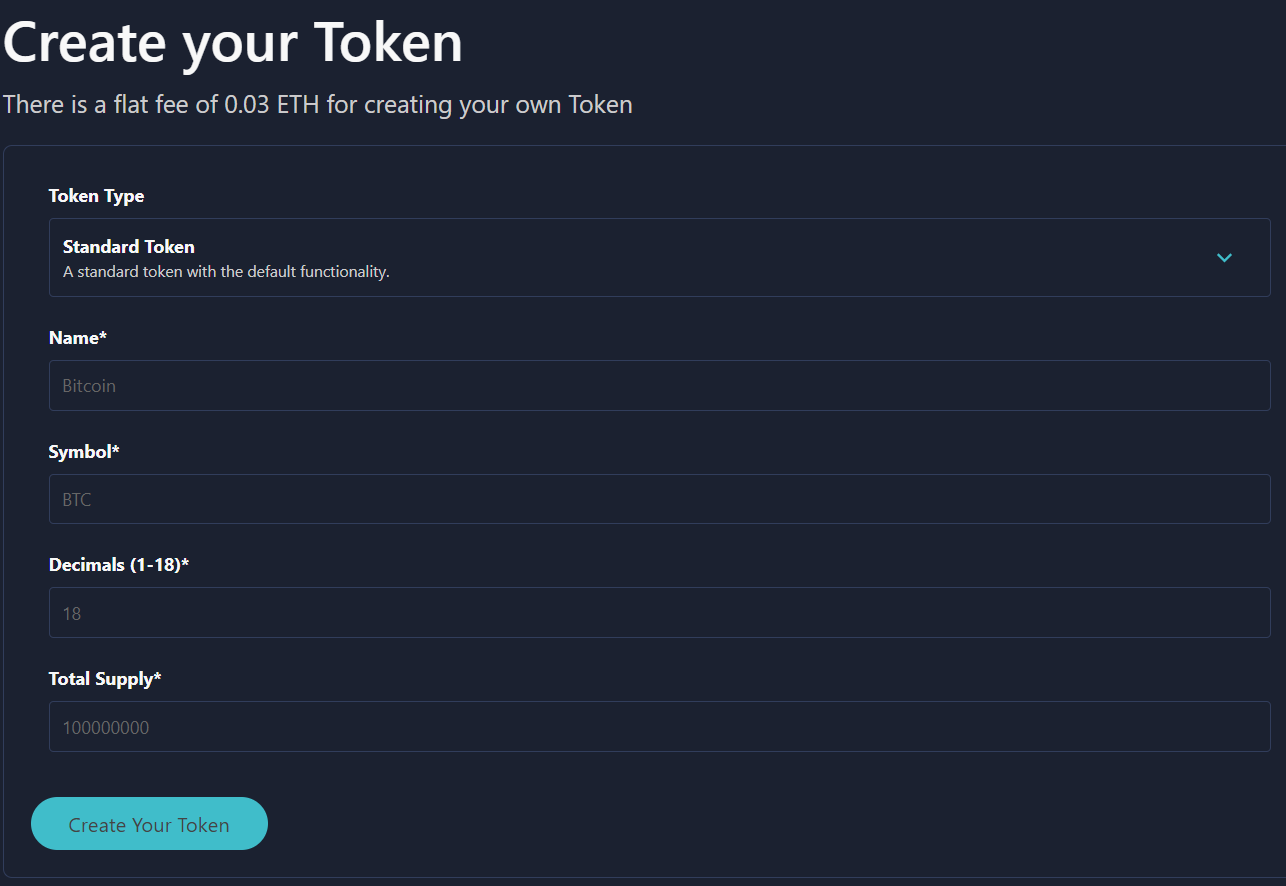
You can easily create an ERC-20 token even if you don't have any programming knowledge with platforms like Coinscope. Coinscope has a token generator that makes ERC-20 token creation as simple as a few clicks.
Coinscope offers various token types:
- Standard Token: Offers fundamental ERC-20 token features.
- Liquidity Generator: Distributes taxes back into the liquidity pool.
- Dividend Token: Distributes dividends to token holders.
- Custom Token: Tailored token creation with advanced features.
Coinscope understands that every project has unique requirements and objectives. That's why they offer additional options for creating Liquidity and Dividend tokens, ensuring that each token meets the specific needs of their clients. Whether you're prioritizing liquidity provision, dividend distribution, or other functionalities, Coinscope will empower you to tailor the token to your project's exact specifications, ensuring optimal performance and effectiveness in the market.
How to Ensure The Security of Your ERC20 Tokens?
To ensure the security of your ERC20 tokens, consider engaging Cyberscope for a comprehensive security audit. With its expertise in cyber security and blockchain technology, Cyberscope can conduct a thorough review of your token smart contracts. This audit process involves defining the scope of the assessment, analyzing the codebase for potential vulnerabilities, and providing detailed recommendations for improvement.
Once the audit is complete, you'll receive a comprehensive report outlining any identified weaknesses and suggested security measures. It's crucial to prioritize the implementation of these recommendations to enhance the overall security posture of your ERC20 token ecosystem. By working with Cyberscope and continuously monitoring for emerging threats, you can maintain the integrity of your tokens and instill confidence in your users regarding the safety of their assets.
How To Choose a Smart Contract Audit Firm?
Selecting a proficient firm to audit your smart contracts is critical for ensuring the security and integrity of your project. It's essential to opt for a reputable company with extensive experience and expertise in blockchain security. Cyberscope emerges as a top choice in this regard, boasting a solid track record in cybersecurity and blockchain technology.
With Cyberscope, you benefit from a team of seasoned professionals who meticulously assess your smart contracts to identify and mitigate potential vulnerabilities. Leveraging advanced tools like Cyberscan, Cyberscope delivers comprehensive audits, providing you with the assurance that your smart contracts adhere to the highest security standards. Choosing Cyberscope instills confidence in the reliability and safety of your project's smart contracts, safeguarding your assets and reputation in the dynamic landscape of blockchain technology.

What are the Audit Steps for ERC-20?
Conducting an ERC-20 audit involves several crucial steps to ensure the security, reliability, and functionality of the token smart contracts. Here's an overview of the typical process followed for an ERC-20 audit:
1. Starting the Interaction:
- Define the scope of the audit, considering factors such as the complexity of the smart contracts, the level of interaction with external systems, and the criticality of the token functionality.
- Determine the objectives of the audit, such as identifying security vulnerabilities, ensuring compliance with the ERC-20 standard, and optimizing contract efficiency.
- Establish clear communication channels and points of contact between the audit team and the client to facilitate information exchange and feedback throughout the process.
- Set realistic timelines and milestones for the audit, taking into account factors such as contract complexity, resource availability, and project constraints.
2. Code Review:
- Perform a line-by-line review of the smart contract codebase, focusing on areas prone to vulnerabilities and security risks.
- Pay particular attention to functions responsible for token transfers, allowances, and approvals, as well as any external dependencies or interactions with other contracts.
- Verify the implementation of access control mechanisms, input validation checks, and error handling routines to prevent unauthorized actions and mitigate potential exploits.
- Evaluate the use of external libraries, dependencies, and third-party components for security vulnerabilities and compatibility issues.
3. Static Analysis:
- Utilize static analysis tools and techniques to analyze the smart contract code for potential security vulnerabilities, code smells, and anti-patterns.
- Conduct automated scans and code inspections to identify common issues such as integer overflows, reentrancy vulnerabilities, and unchecked function calls.
- Evaluate the complexity and readability of the codebase, identifying areas that may require refactoring or optimization for better maintainability and performance.
4. Dynamic Testing:
- Deploy the smart contracts to a test network or sandbox environment to simulate real-world interactions and behavior.
- Execute a comprehensive suite of test cases covering various scenarios, edge cases, and boundary conditions to validate the correctness and robustness of contract functionalities.
- Monitor contract execution and transaction outcomes to detect any unexpected behavior, exceptions, or errors that may indicate underlying issues or vulnerabilities.
5. Security Assessment:
- Conduct a holistic assessment of the smart contracts' security posture, considering factors such as data confidentiality, integrity, and availability.
- Identify and prioritize potential attack vectors, threat scenarios, and security risks based on their likelihood and potential impact on the contract and its users.
- Evaluate the effectiveness of existing security controls, access controls, and authorization mechanisms in mitigating identified risks and preventing unauthorized access or manipulation of contract assets.
6. Documentation and Reporting:
- Compile audit findings, observations, and recommendations into a comprehensive audit report, organized in a clear and structured format.
- Provide detailed explanations of identified vulnerabilities, including their root causes, potential impact, and recommended remediation strategies.
- Include supporting evidence, code snippets, diagrams, and relevant references to enhance the clarity and credibility of the audit findings.
- Tailor the report to the intended audience, ensuring that technical details are presented concisely and comprehensively for stakeholders with varying levels of expertise.
7. Client Communication:
- Schedule regular meetings and checkpoints with the client to review audit progress, discuss interim findings, and address any questions or concerns.
- Foster open communication and collaboration between the audit team and the client, encouraging active participation and feedback throughout the audit process.
- Provide guidance and support to the client in interpreting audit findings, prioritizing remediation efforts, and implementing recommended security enhancements.
8. Follow-Up and Support:
- Offer post-audit support and assistance to the client during the remediation phase, including clarification of audit findings, guidance on best practices, and assistance with code changes.
- Conduct follow-up assessments and validations to verify the effectiveness of remediation measures and ensure that identified vulnerabilities have been successfully addressed.
- Encourage ongoing monitoring and maintenance of the smart contracts to proactively identify and mitigate emerging security threats and vulnerabilities.
What is The Cost of an ERC-20 Token Audit?
The cost of an ERC-20 audit can vary significantly depending on several factors, including the complexity of the smart contract code, the depth of the audit required, the reputation and expertise of the auditing firm or consultant, and the specific services included in the audit package.
Generally, ERC-20 token audits can range from a few thousand dollars to tens of thousands of dollars or more, depending on the scope and requirements of the audit. Simple audits may focus on basic security checks and code review, while comprehensive audits may involve in-depth analysis, vulnerability assessments, and extensive testing using specialized tools and methodologies.
Factors that can influence the cost of an ERC-20 audit include:
- Scope of Audit: The breadth and depth of the audit, including the number of smart contracts to be reviewed, the complexity of the codebase, and the specific functionalities and features of the ERC-20 token.
- Type of Audit: Different types of audits, such as code review, security assessment, compliance analysis, and formal verification, may have varying costs based on the level of expertise and effort required.
- Auditing Firm or Consultant: The reputation, expertise, and track record of the auditing firm or consultant can impact the cost of the audit. Well-established firms with a proven track record may command higher fees than newer or less experienced auditors.
- Additional Services: Additional services such as post-audit support, code remediation, and ongoing monitoring may incur additional costs beyond the initial audit fee.
- Timeline and Turnaround: Urgency and timeline requirements can affect the cost of an ERC-20 audit. Expedited audits or shorter turnaround times may come with higher fees to prioritize resources and expedite the review process.
It's important to discuss the specific requirements and expectations of the ERC-20 audit with potential auditing firms or consultants to obtain accurate cost estimates and ensure transparency regarding pricing, deliverables, and timelines.
What Are The Consequences of Choosing Not to Proceed with an Audit?
If you decide against proceeding with an audit, several potential outcomes could arise. Firstly, your smart contract may harbor undetected vulnerabilities or security flaws, leaving it susceptible to exploitation by malicious entities. Such vulnerabilities could lead to financial losses, regulatory non-compliance, and damage to your project's reputation. Moreover, investors and users may lose confidence in your project's security measures, potentially hindering adoption and growth. Security incidents stemming from unaudited smart contracts can have significant repercussions, emphasizing the importance of prioritizing audits to mitigate risks and ensure the trustworthiness of your project in the blockchain ecosystem.

Conclusion
In the rapidly evolving landscape of blockchain technology and decentralized finance (DeFi), ERC-20 tokens have emerged as the backbone of tokenization and digital asset management on the Ethereum blockchain. Their standardized framework, interoperability, and compatibility have fueled innovation, liquidity, and accessibility within the cryptocurrency ecosystem. However, with innovation comes the imperative for security and compliance.
Cyberscope, a leading cybersecurity company with a strong presence in the cryptocurrency and blockchain space, offers specialized services tailored to the needs of ERC-20 tokens and blockchain projects. With a track record of auditing numerous projects, securing assets, and providing KYC services, Cyberscope stands at the forefront of ensuring the security, integrity, and compliance of ERC-20 tokens. Through its automated contract analysis tool, Cyberscan, and partnerships with industry leaders like CoinMarketCap and CoinGecko, Cyberscope provides comprehensive security audits, vulnerability assessments, and compliance checks to safeguard ERC-20 tokens against emerging threats and regulatory challenges.
In conclusion, ERC-20 tokens represent a transformative force in the cryptocurrency ecosystem, driving innovation, interoperability, and democratization within decentralized finance. With Cyberscope's expertise and commitment to security, ERC-20 token projects can navigate the complexities of blockchain technology with confidence, resilience, and integrity.

.png%3Falt%3Dmedia&w=640&q=75)

