

What is Sleep Minting? Everything You Need to Know

Have you ever heard that someone minted an NFT inside someone else's wallet but has full access to it to transfer or sell it anywhere? If not, then don’t worry; this guide is the perfect opportunity to learn something new happening in the cryptocurrency industry.
As we all know, NFTs have become very popular. According to a report by Coingecko, the NFT sector is projected to move around $800 billion by 2024, fueled by the rising interest in metaverse and gaming.
But popularity also comes with risks and threats.
A similar risk rising these days is Sleep Minting. This happens when a trickster gets permission to make an NFT look like it came from a famous person's digital wallet without them knowing. It seems the actual creator made the NFT, but then it secretly ends up with the trickster instead.
In this article, we're going to explain what Sleep Minting is and how it affects the market for NFTs. We'll also share tips on how to avoid getting tricked by related scams.
What is Sleep Minting?
To put it simply, Sleep Minting is when a scammer employs a deceptive tactic where they mint an NFT and promptly deposit it into the wallet of a well-known creator. This strategy is designed to create a misleading appearance, making it seem as if the creator personally initiated the NFT creation but then transferred it to the scammer.
Essentially, the scammer exploits the trust associated with the creator's reputation to carry out fraudulent activities in the NFT space. For example, not too long ago, somebody pretended to be Beeple – a trendy digital artist – and sold one of these fake pieces for a lot of money by taking advantage of Beeple's fans who thought it was real.

How Does Sleep Minting Work?
Understanding the mechanics of Sleep Minting involves delving into the details of how NFT provenance and ownership are stored in smart contracts, particularly those following the ERC-721 Standard.
Smart contracts typically allow anyone to query information, such as the current owner of an NFT, using the ownerOf(tokenId) function. Additionally, variations in the eth_call RPC method parameters enable querying for NFT ownership at specific block numbers. However, the most straightforward method involves analyzing ERC-721 Transfer Event logs.
A Transfer Event log serves as a communication tool between a smart contract and the external world, containing vital details about an NFT transfer. This information includes who the NFT is transferring from, who the NFT is transferring to, and the unique token ID being transferred. Transfer Event logs provide an efficient means of verifying an NFT's provenance.
The deceptive aspect of Sleep Minting arises from the malleability of the data emitted in an Event log. Ordinarily, one would expect their address to appear in the "from" field of a Transfer Event log when initiating an NFT transfer. However, Sleep Minting allows a scammer to reclaim a sleep-minted NFT from a famous creator while artificially placing the creator's address in the "from" field.
In more granular detail, here's how Sleep Minting operates:
1. Minting with Permissions
A scammer mints an NFT to a wallet associated with a famous creator while maintaining permission to reclaim or withdraw that NFT from the creator's wallet.
2. Reclaiming the NFT
The scammer executes a transaction to reclaim the NFT from the famous creator. Despite the scammer initiating this transaction, they can manipulate the "from" field of a Transfer Event log, making it seem as if the famous creator legitimately transferred the NFT.
3. Deceptive Transfer
The scammer now possesses an NFT that appears to be authentically created and previously owned by the famous creator. This misleading provenance can be leveraged to sell the NFT at an inflated price.
Is Sleep Minting a Threat to the NFT Market?
Sleep Minting poses a significant risk to the NFT market by shaking the foundations of trust upon which the entire ecosystem relies. Trust is essential in any financial market, and in the world of NFTs, it hinges on the belief that the details of provenance and ownership are accurate and transparent. Investors and collectors depend on the integrity of blockchain technology, smart contracts, and associated data to verify the legitimacy of NFTs.
The impact of Sleep Minting is felt in the confidence of users regarding the authenticity of NFTs. The success of the NFT market relies on the belief that creators genuinely mint and transfer their NFTs, reflecting the true origin and ownership of these digital assets. Sleep Minting introduces doubt about this authenticity, creating a potential barrier for investors who may become hesitant to participate in the market.
Also Read: The Top 10 Cryptocurrency Hacks Of All Time
How to Sleep Mint NFTs?
Disclaimer: Now, we’ve come to one of the most crucial parts of this topic. Please keep in mind that this section is for educational purposes only, and we don’t encourage you or anybody else to sleep mind NFTs and scam people. It is considered unethical and should also be treated as such.
So I think you understand the advice, so let’s get into the technical part of this topic, but I’ll be explaining all of it in a non-technical way so you can get the hang of it.
API and Smart Contract Deployment
Firstly, you need a place from where you can deploy the smart contract for the NFT you’ll be creating. For that, you can use Alchemy, which not only offers API to its users, but if you visit their website, they have a whole section from where you can learn how to mint an NFT.
Also, be aware that Alchemy doesn’t allow sleep minting as this whole thing is dependent on the complexities of the smart contract deployment. Don’t worry; you’ll know what this means ahead.
Blockchain and Ownership
The concept of Blockchain relies on the digital ownership of the assets in the ecosystem. But can anyone have access to someone’s wallet just like that? And the answer to that is no. If this were the case, many famous people with tons of cryptocurrency lying around would have been robbed till now.
So, if the scammer doesn’t have access to the target’s wallet, then how is he orchestrating this whole thing? The answer is simple; as Keir Finlow-Bates also said, it’s all a confidence trick that is divided into two steps:
- Mint NFT in a Famous person’s wallet
- Transfer the NFT out of the wallet and into your own
Now let’s take a detailed look at both of these steps:
Step 1: Mint NFT in a Famous Person’s Wallet
The first step is to mint the NFT, but for that, we need to deploy a smart contract. You can find the NFT tutorial code on how to mint an NTF in Alchemy from where you can learn if you don’t already. Now, once you have deployed the smart contract, and part of the code looks like this:
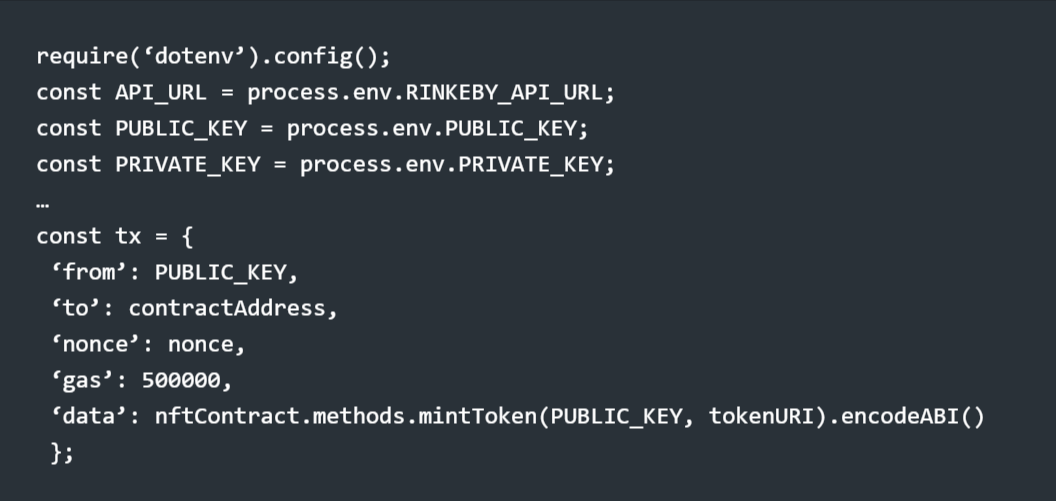
Now, the only change you need to make to transfer the NFT (or seemingly make it look like it) into Beeple’s account is to add (const BEEPLE_KEY = "0xc6b0562605D35eE710138402B878ffe6F2E23807”) inside the code. Once executed, it will look like this:
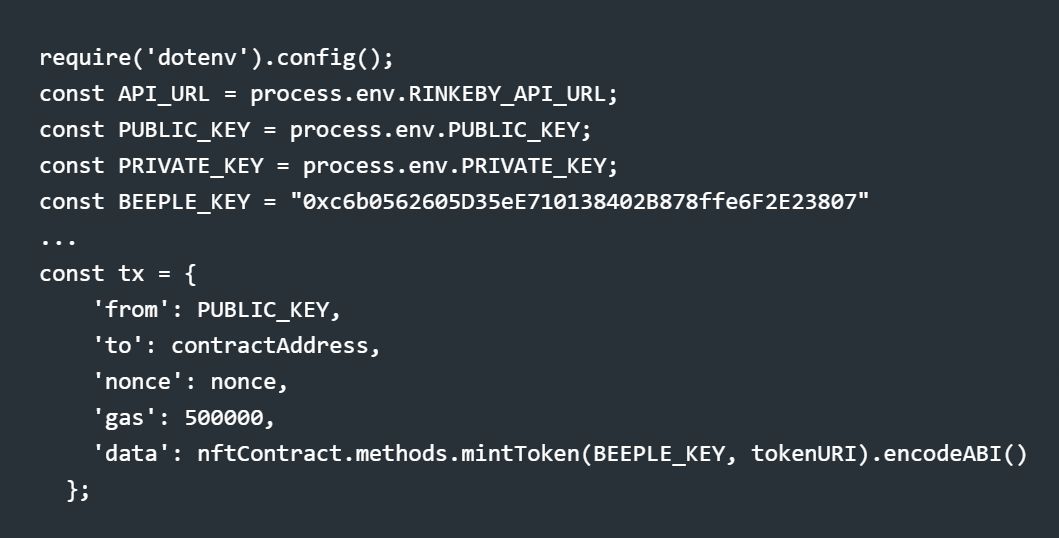
Observe that the nftContract.methods.mintToken function in the second code block uses BEEPLE_KEY instead of your own PUBLIC_KEY.
But what happens next? The minting transaction would look something like this at the bottom of the token entry on OpenSea.io:
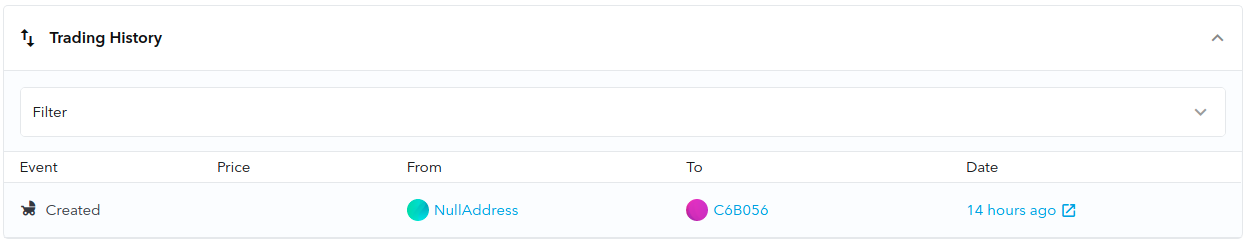
With this example, it becomes evident that assuming the origin of a token based on the initial transaction (involving minting and transfer from the 0x000000 address to a personal Ethereum address) is a flawed premise.
Step 2: Transfer the NFT out of the wallet and into your own
Now, this section is fairly technical, so I’ll just explain how it's done in simple words. Let’s see what a scammer does to allow himself access to the NFT.
Backdoor into Contract Ownership
In the pursuit of making it appear as though Beeple minted the NFT token, he exploits the code structure provided by OpenZeppelin in the ERC721 contract.
By inserting a new variable in the Ownable.sol contract and tweaking the onlyOwner() function, he ensures that one of their Ethereum addresses becomes a secret owner alongside Beeple, granting them a backdoor into the ownership of the contract.
This manipulation allows the scammer to transfer ownership to Beeple while maintaining the capability to reclaim it using their backdoor.
Token Ownership Manipulation
To further control the narrative, he extends his influence over token ownership. Through strategic modifications in the ERC721.sol template, the scammer ensures that actions on the token, such as approving a transfer, can be executed not only by the token owner but also by their backdoor address.
This process involves subtle additions to the approve() and _isApprovedOrOwner() functions, providing the scammer with nuanced control over the token's destiny. The entire procedure, involving minimal changes to Ownable.sol and ERC721.sol, represents that he carefully planned these changes to show that the original work wasn't as difficult as it seemed.
The Result
So after all the work, including deploying the modified contract, creating another token under Beeple's name, and finally, moving the token to his personal Ethereum address, here’s the final look at the transaction on OpenSea:
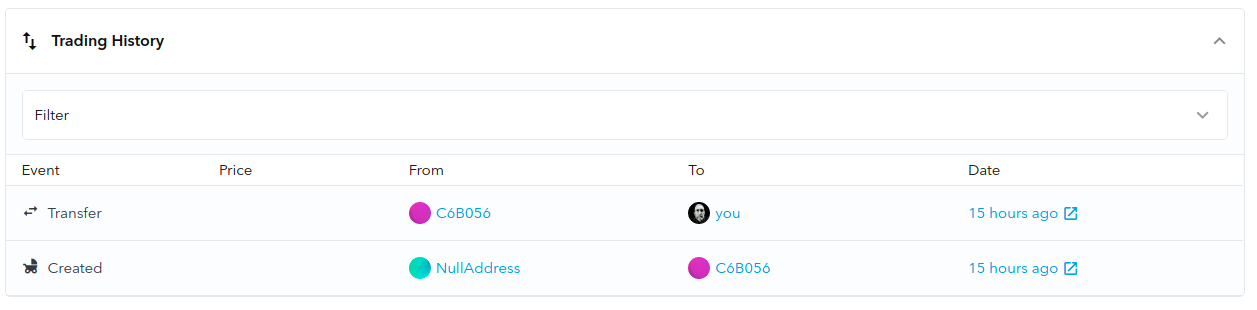
We proved that it isn’t difficult for someone with the right amount of knowledge to execute this scam. So, how are we supposed to keep ourselves safe from such scams? The answer to it is ahead.
How to Protect Yourself from Sleep Minting Scams
To shield yourself from sleep minting scams, always double-check where an NFT comes from before you accept it. If the minting address seems fishy, do some digging. And if an NFT mysteriously appears from an unknown source, don't think twice – Just delete it.
If you want to spot a sleep minted NFT, here’s how:
- Verify Legitimacy: Always check if the NFT is legit. Look into past transactions on the blockchain and ensure the seller is trustworthy.
- Use Etherscan’s Token Viewer: It's like NFT detective work. Etherscan can help you check if the token you want has any sleep-minting history.
Preventing Sleep Minting
Now, how about stopping sleep minting in its tracks? Here are some simple steps:
- Watch Out Who Mints into Your Wallet: If you're a creator, be cautious about letting just anyone mint NFTs into your wallet.
- Keep an Eye on Your Wallet: Stay vigilant. Regularly check your wallet for anything suspicious. If something looks off, investigate.
- Withdraw Funds Pronto: If an NFT ends up in an unexpected address, withdraw those funds immediately. Don't let the scammer run away with your hard-earned money.
Quick Link: Victim of a Crypto Scam? See How You Can Recover Your Funds
Targets for Sleep Minting Scams
Now, who do these scammers target the most? It's the big shots, the high-profile creators with a massive fan following. Why? Because they get a ton of requests, and scammers find it easier to trick them. These creators might also be a bit lax in checking the origin of incoming NFTs, making them prime targets.
Final Thoughts
So, that was it. It was honestly quite a long debate. We've covered quite a bit about NFTs and the tricky business of sleep minting. As the NFT universe expands, it's crucial to be vigilant and proactive to protect your investments and maintain trust in the market.
In this evolving landscape, awareness is your shield. Whether you're a creator, buyer, or enthusiast, staying informed about potential threats like sleep minting is your armor. The NFT market is a dynamic space filled with innovation and creativity, but like any flourishing ecosystem, it's not without its challenges.

.png%3Falt%3Dmedia&w=640&q=75)

